The bionic SOC is here
We are transforming cybersecurity operations with human + AI collaboration.
We’ve built the decision fabric of the human-AI SOC
Our AI prioritizes key alerts, threat intelligence, and data to accelerate and automate investigations and enrichment.
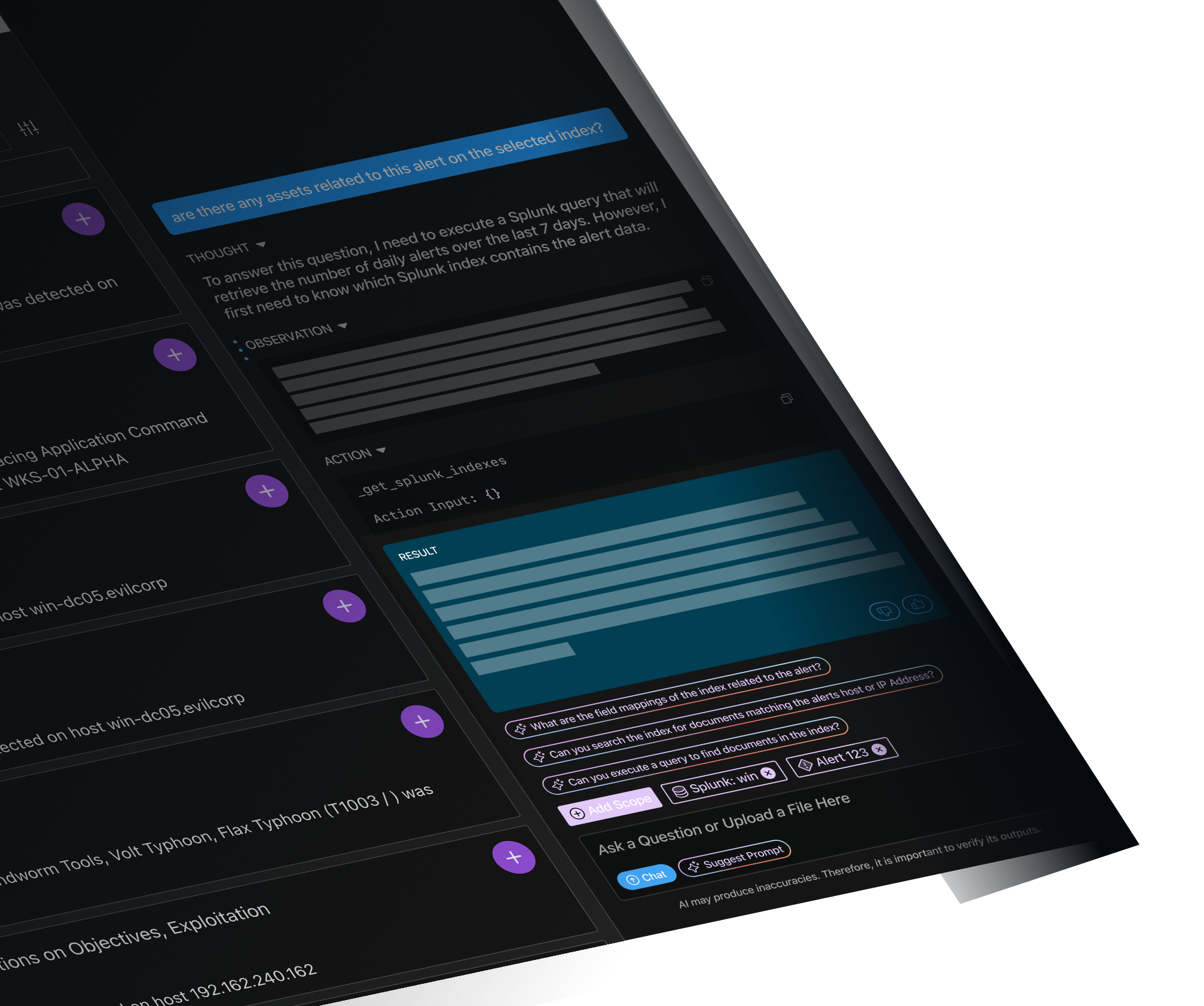
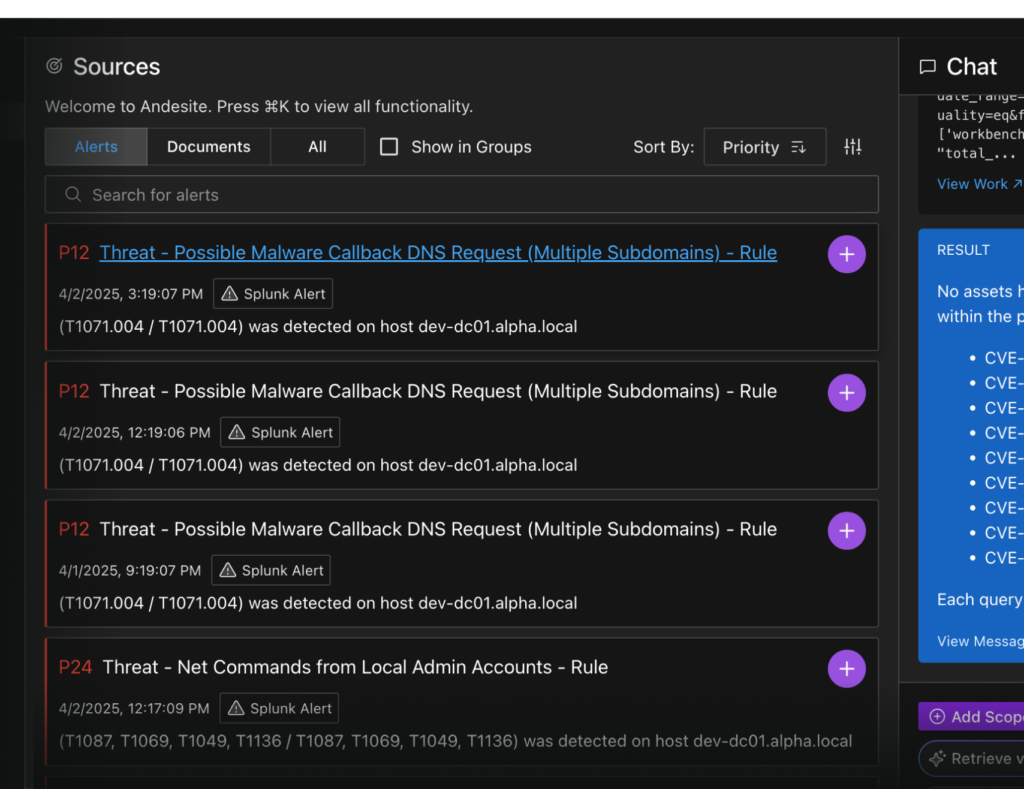
The investigation workspace for SOC Teams
Automate investigation, alert management and enrichment.
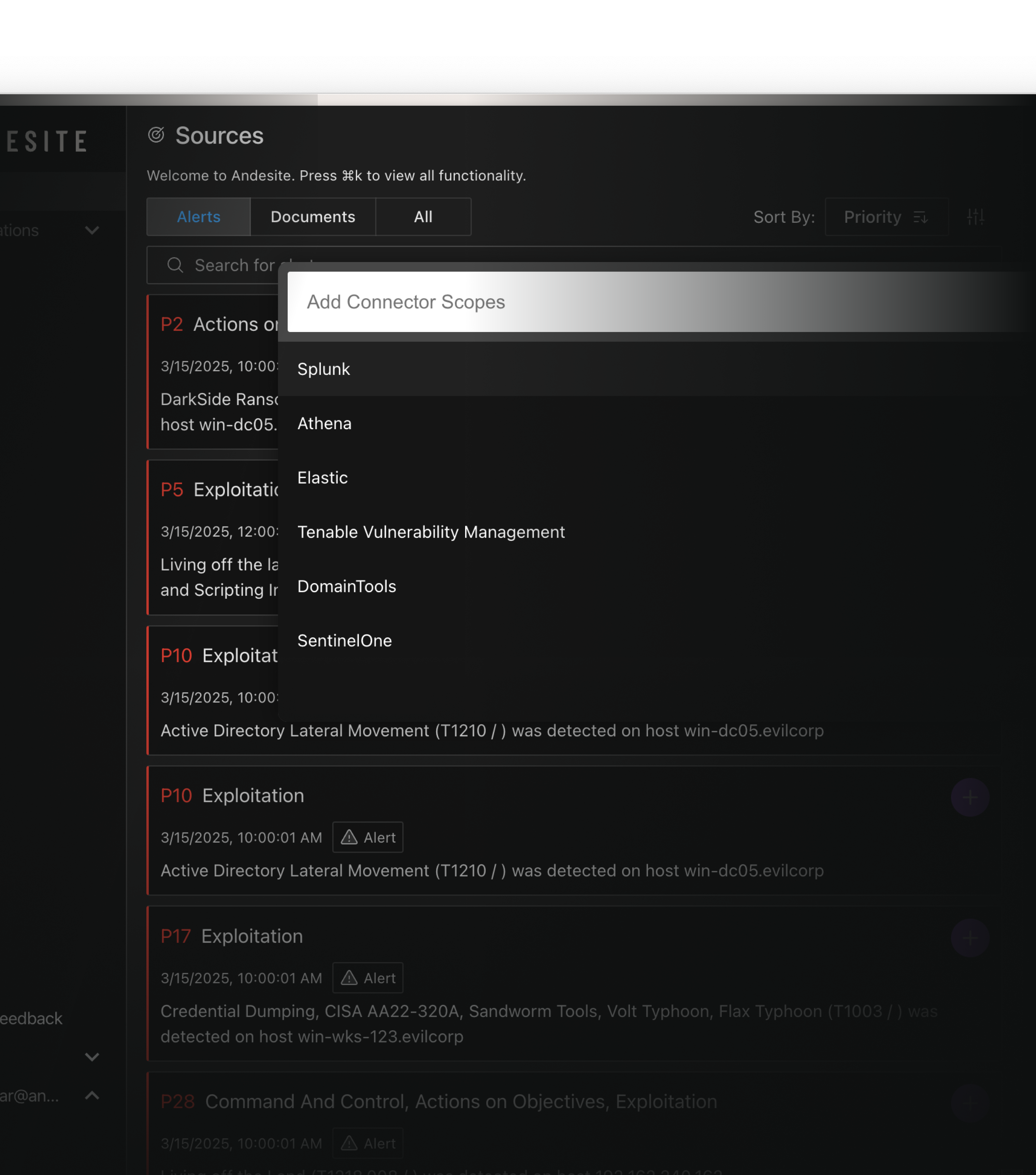
×Add multiple sources to the scope of a single investigation.
×Accelerate time to investigate and respond with AI-driven workflows and visualizations.
×Collaborate to assess and determine risk levels.
×
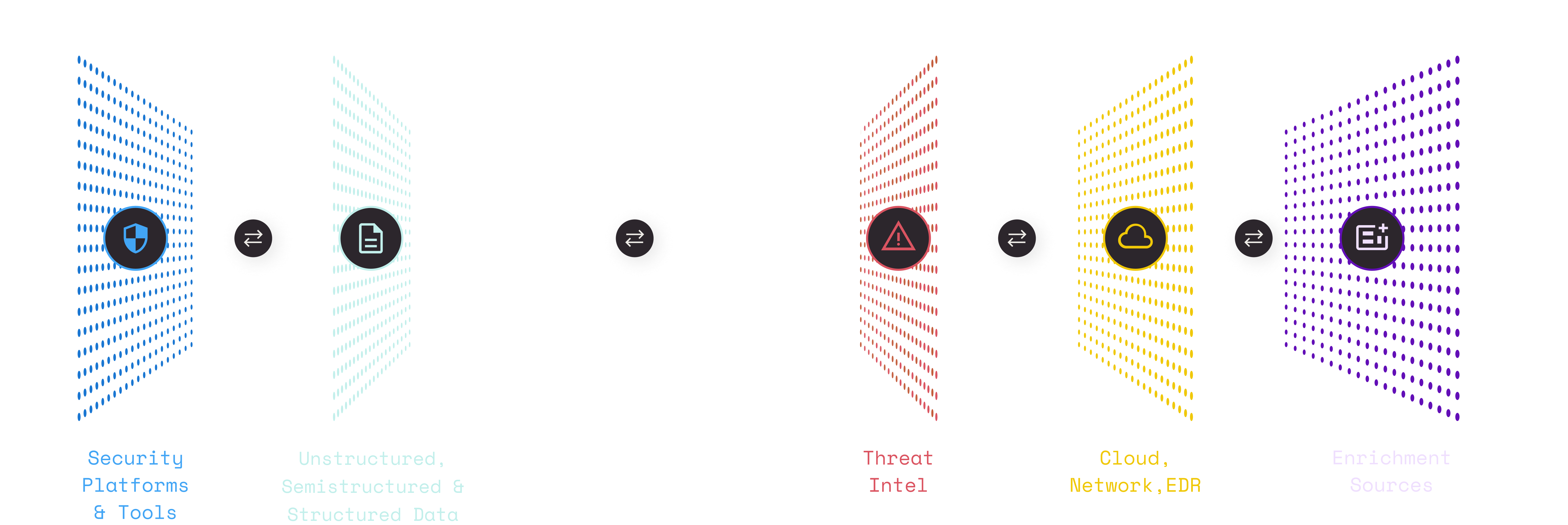
Unified views, connected workstreams
Connect workstreams and data silos on the same view across security platforms and tools, and get alerts from multiple sources, prioritized in the same list.
No ETL required
No data migration or extraction needed, no delays
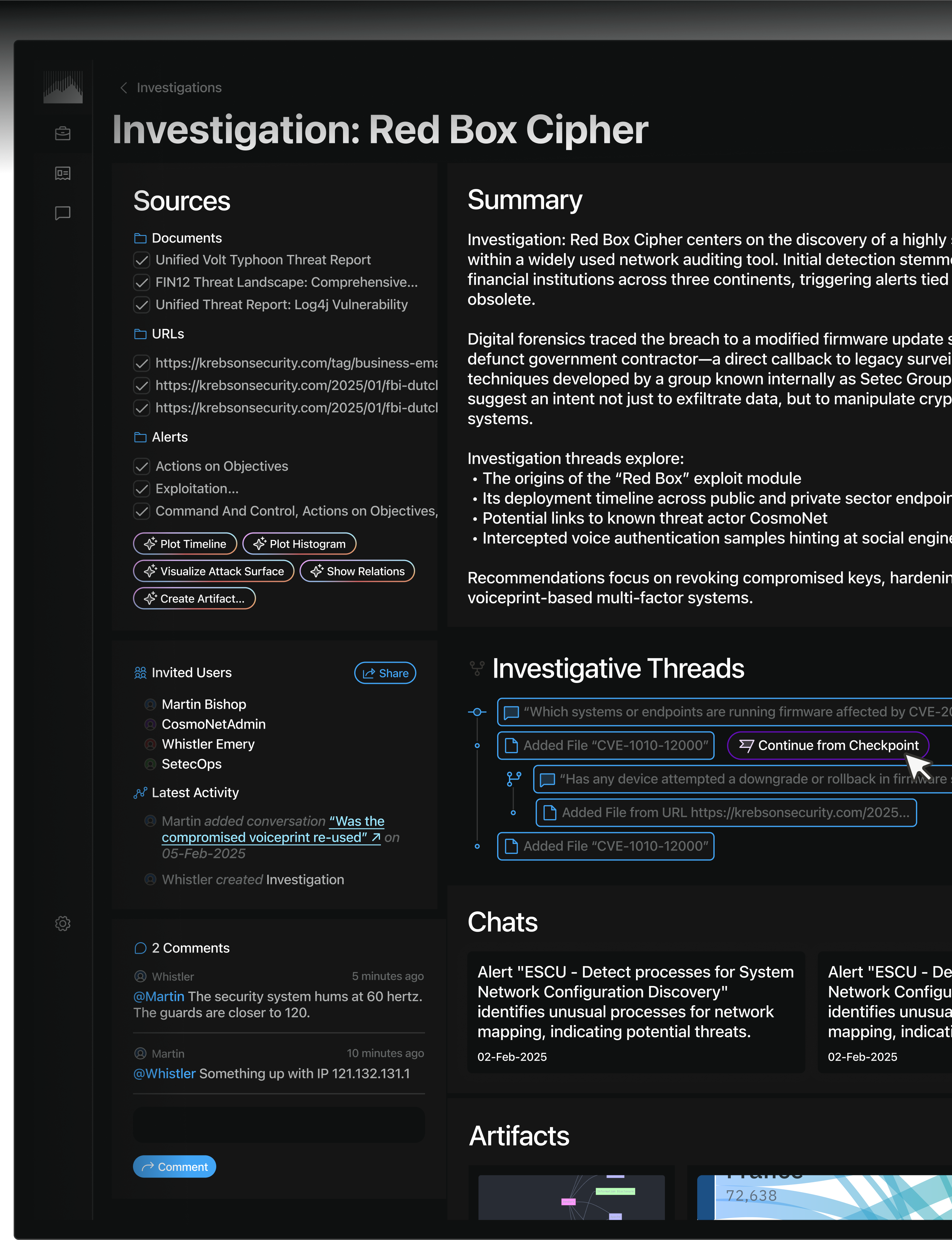
Evidentiary AI™
AI-driven investigations can be traced back to verified sources and insights so humans can review and replay the analysis.
Safe AI Architecture™
We’ve built guardrails to protect your network, your data, and your customers’ data.
Contextual Awareness
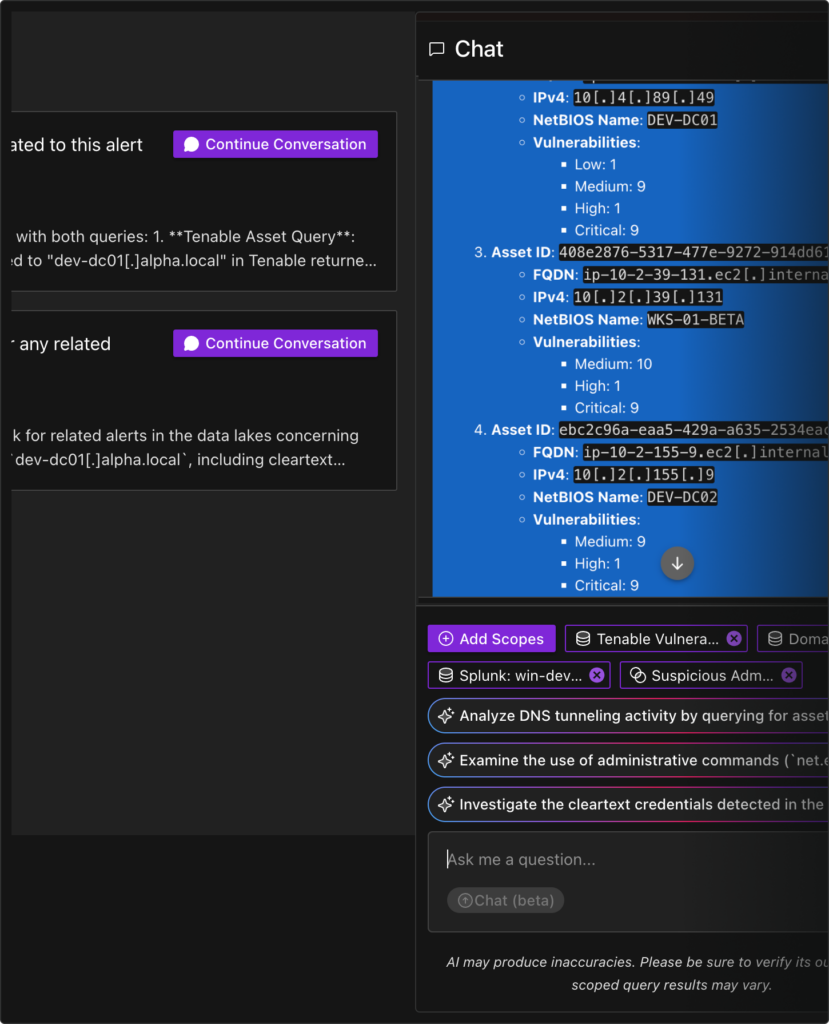
Our AI proactively combs data sources, surfaces and prioritizes key indicators, connects the dots, and unlocks insights within the scope of a single investigation.
Secure and compliant
by design

- Built-in continuous security, compliance, privacy, and AI safety for the highest standards and requirements of both public and private sectors.
- Aligned with FedRAMP High, SOC 2, NIST 800-53 (High), NIST CSF, ISO 27001, ISO 27701, ISO 42001, PCI DSS, HIPAA and AI RMF requirements.
- Trust Center documenting our security posture and over 450 continuous monitoring controls.
- Cloud and self-managed on-prem options.
How we elevate Cybersecurity Operations
Use Case
Alert Investigation
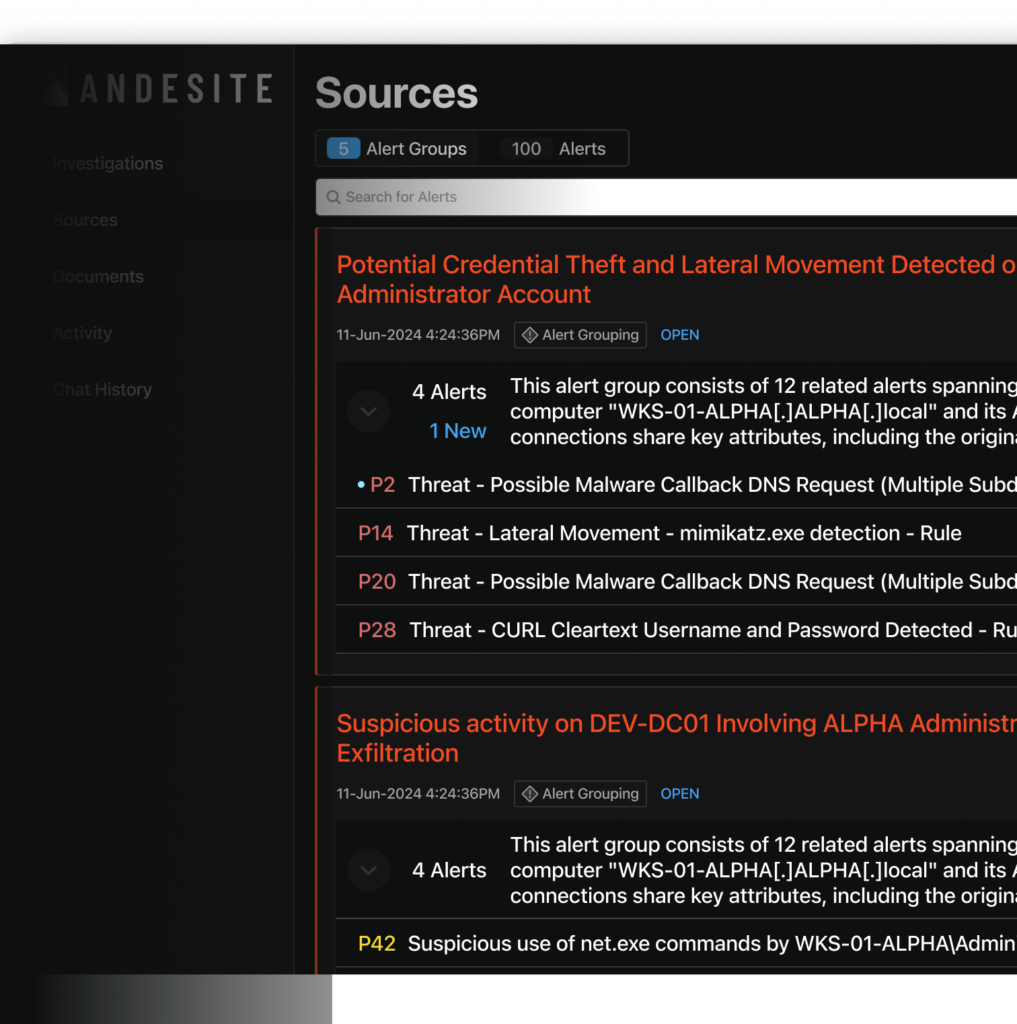
- Access alerts from multiple sources prioritized and consolidated in a single view.
- Add multiple sources to the scope of a single investigation.
- Process high-volume alerts at high speed.
- Execute alert triage and report with verifiable, traceable evidence.
Use Case
Threat Hunting
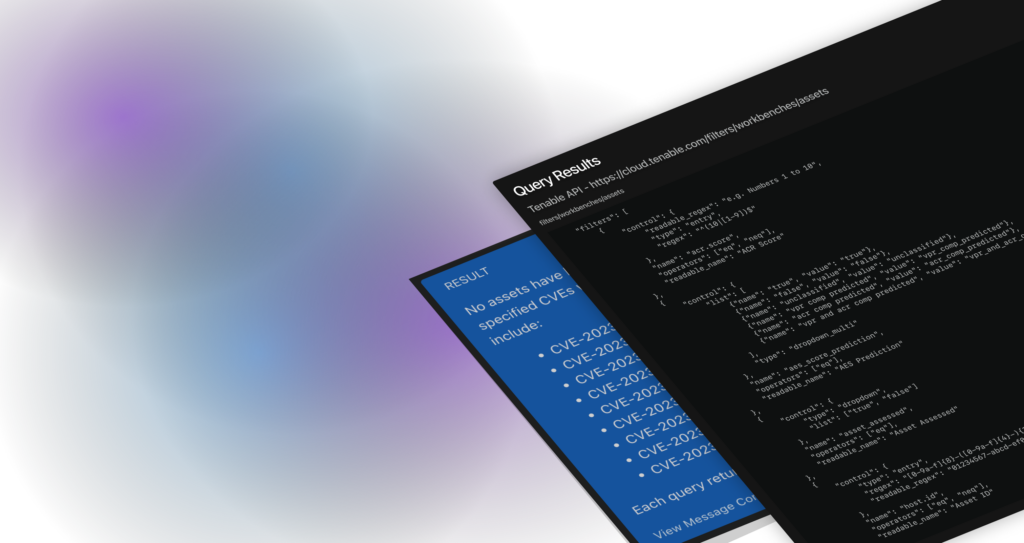
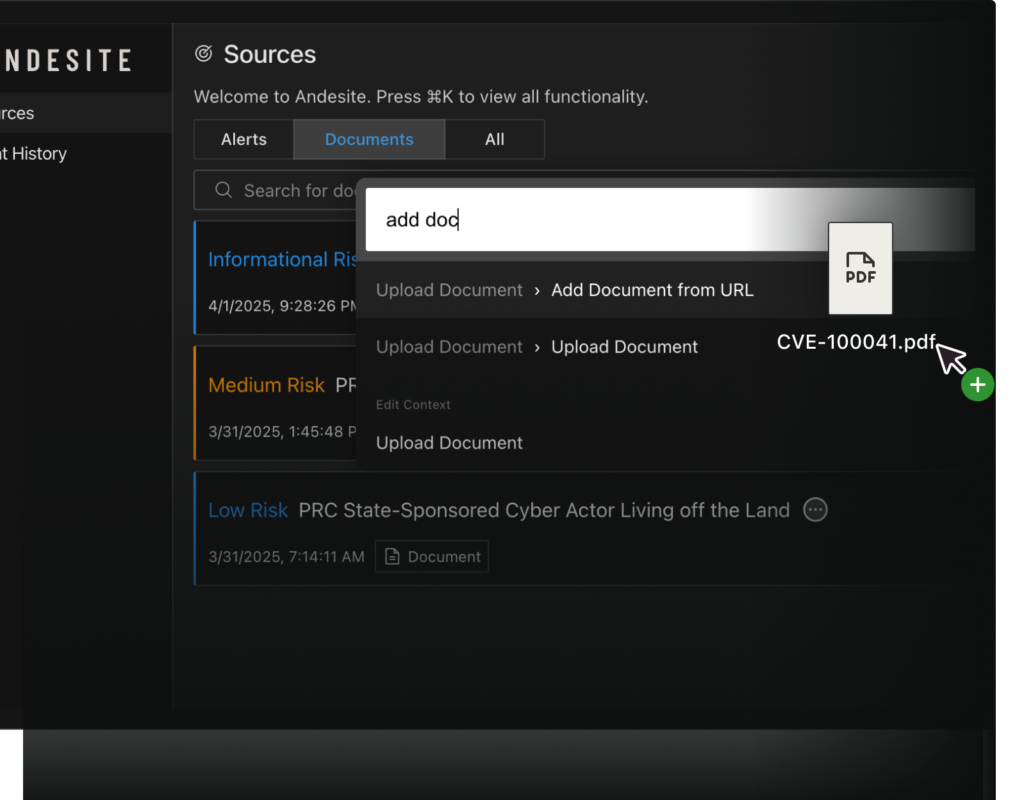
- Initiate the investigation where you are, with a query, uploading a document, or from an url.
- Determine threat level.
- Identify the blast radius with contextual awareness capabilities.
Use Case
Threat Intelligence Operationalization
- Initiate investigation directly from the intelligence source, including URLs and PDFs.
- Add multiple sources to the scope of a single investigation.
- Determine threat relevance and level.
- Accelerate time to detection with automated investigation and enrichment.
Request a Demo
To learn more about the Human-AI SOC, request a demo.