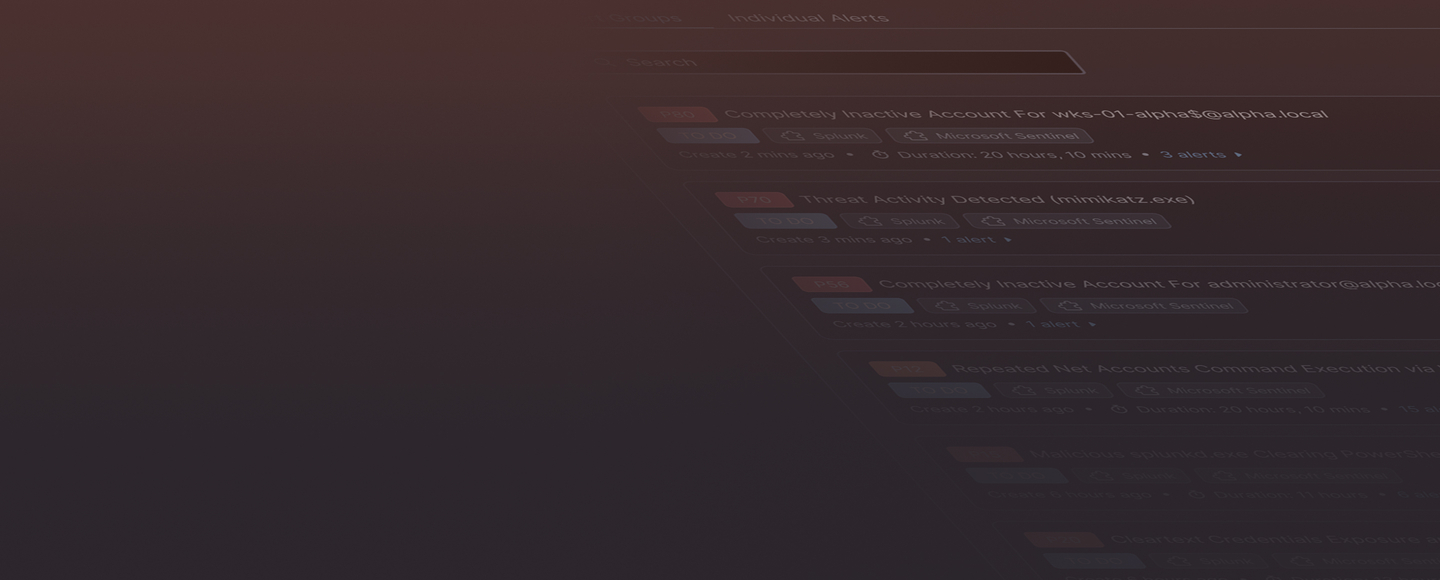
The Workspace for SOC teams
- Prioritize alerts from multiple sources in a consolidated view.
- Automate investigation, high-volume alert management, and enrichment.
- Initiate investigation directly from the intelligence source, including urls and PDFs.
- Add multiple sources to the scope of a single investigation.
- Accelerate time to investigate and respond
- Collaborate to assess and determine risk levels.

Safe Al Architecture™
Benefit from a flexible and safe architecture that adapts to your use cases, tools, and workflows – all while protecting your applications and data.
Contextual Awareness
Thanks to Andesite’s contextual awareness, you get the actionable insights that matter to your organization’s specific risk profile.

No ETL Required
Enjoy less exposure, enhanced security, no migrations, and no delays.
Evidentiary AI™
Be audit-ready with AI-driven investigations that can be traced back to verified sources and insights.

Multiple Deployment Options
Andesite can be deployed on SaaS, air-gapped self-managed, and hybrid environments.
Use Cases

Alert Investigation
Investigate and prioritize alerts from multiple sources in a unified view, using AI-assisted context and enrichment to rapidly assess risk and drive confident decisions.

Cloud
Correlate and enrich cloud activity across logs and signals to quickly identify suspicious behavior and understand its context and impact.

End Point
Analyze and correlate endpoint activity to reconstruct timelines, assess scope and blast radius, and determine appropriate response actions.

Identity and Access
Detect and investigate identity-based threats such as credential misuse, anomalous access, and privilege abuse to quickly confirm risk and contain impact.

Network
Identify and investigate unusual network traffic patterns, including lateral movement and cross-signal activity, to uncover hidden or emerging threats.

Phishing
Swiftly identify phishing threats, investigate, and reduce attack risk.

Ransomware
Identify ransomware indicators early, assess potential impact, and support rapid containment to reduce operational and organizational risk.

Threat Hunting
Initiate investigations from analyst-driven entry points—including queries, documents, URLs, or alert groups—to proactively uncover threats and determine scope.

Threat Intelligence
Turn threat intelligence into action by launching investigations directly from intel sources (e.g., URLs, PDFs), enriching findings, and determining threat relevance and impact in minutes.
Our Partners
Learn More
For a live product walk through,